Shopped at Vero Moda, Jack Jones Online? Your Data Was at Risk
Vero Moda, Jack and Jones, Only, and other Bestseller India websites had a security flaw that allowed the hijacking of user accounts by anyone who simply knew the targets email ID used for signing up. This would in turn expose information such as the user’s delivery addresses, their full name and phone number, and any saved credits with the sites. Although this information might not worry you, such data is actually highly valuable, and such information is also often used in phishing attacks to impersonate a real business and scam you out of your money. After Gadgets 360 raised the issue with the company — a full year after the security researcher had done so — the flaw was finally fixed, so customers data is no longer accessible, but the company has shared no details on how long customer data was at risk.
Security researcher Sayaan Alam wrote to the company’s executives in September 2019. At the time, Alam tweeted to the company’s CEO and was asked to send an email. Alam then sent a report of the issue to the company’s CEO, and received a tweet in response from Vero Moda India’s account, which said it had “forwarded this to the concerned team.”
In emails reviewed by Gadgets 360, Alam explained that he had been carrying out security testing and found a bug that could allow takeover of accounts for Vero Moda, Jack and Jones, and Only India. He asked to be connected to the company’s CTO.
More than a year later, Alam said he did not receive any further information from the company, while the bug remained active. In December, Alam contacted Gadgets 360, and by creating a dummy account with a secret detail, we were able to confirm that Alam could in fact take over an account if he was aware of the email ID used to sign up.
Given how widely email IDs are used, it wouldn’t be difficult for someone to obtain anyone’s email ID, and then through this, get other details like a person’s home address, compromising their safety and security.
In chats with Gadgets 360, Alam explained that he “did not want to make the issue public while the bug was still active, as that could put user accounts at risk.”
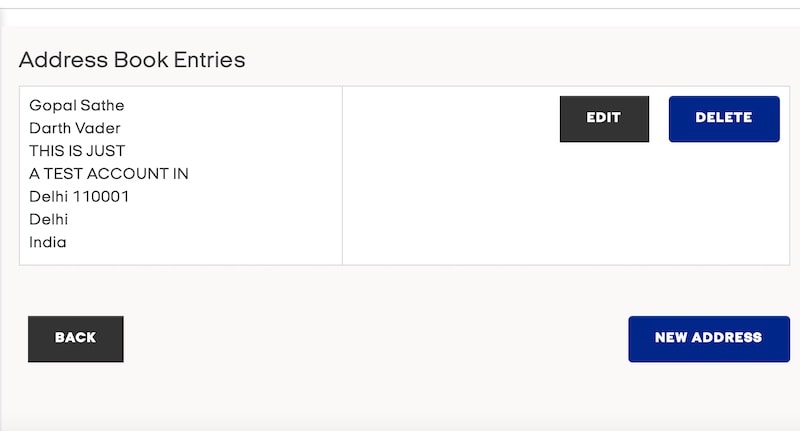
We created a dummy account to test whether the account takeover bug was live
Photo Credit: Screenshot
Gadgets 360 then reached out to the company, and exchanged emails with its Chief Information Officer Ranjan Sharma who responded quickly and collected information about Alam’s findings. After getting the details, Sharma replied that he would “check.” A week later, when asked for updates, Sharma replied that the bug had been fixed.
“First of all let me thank you for bringing this to our notice,” he said via email. “We did a deep dive and found a version issue with our system and hence the token exchange was getting missed out which we fixed the same day. We are also working on a plan to reach out to our registered customers.”
At this point, we asked for information about how many customers use the site, and whether the company has any bug bounty program to encourage security researchers towards bringing in reports. However, Sharma did not share any responses after that and it’s unclear if any users were informed — the test account we created did not receive any updates about its information being breached — three months after the issue was disclosed to the company and the bug fixed.
Sharma and Bestseller responded quickly when contacted by Gadgets and resolved the issue once it was discussed, which is a positive development. However, the lack of communication to users is one area that could certainly be improved upon.
The bug in question, as demonstrated by Alam, was fairly simple, and it is possible that any number of user data could have been compromised by this flaw. However, this is in line with a continuing problem in India, where security researchers are actively discouraged from exploring weaknesses in online systems — and users are rarely, if ever, told about problems unless the matter goes public from other sources.
Does WhatsApp’s new privacy policy spell the end for your privacy? We discussed this on Orbital, the Gadgets 360 podcast. Orbital is available on Apple Podcasts, Google Podcasts, Spotify, and wherever you get your podcasts.



